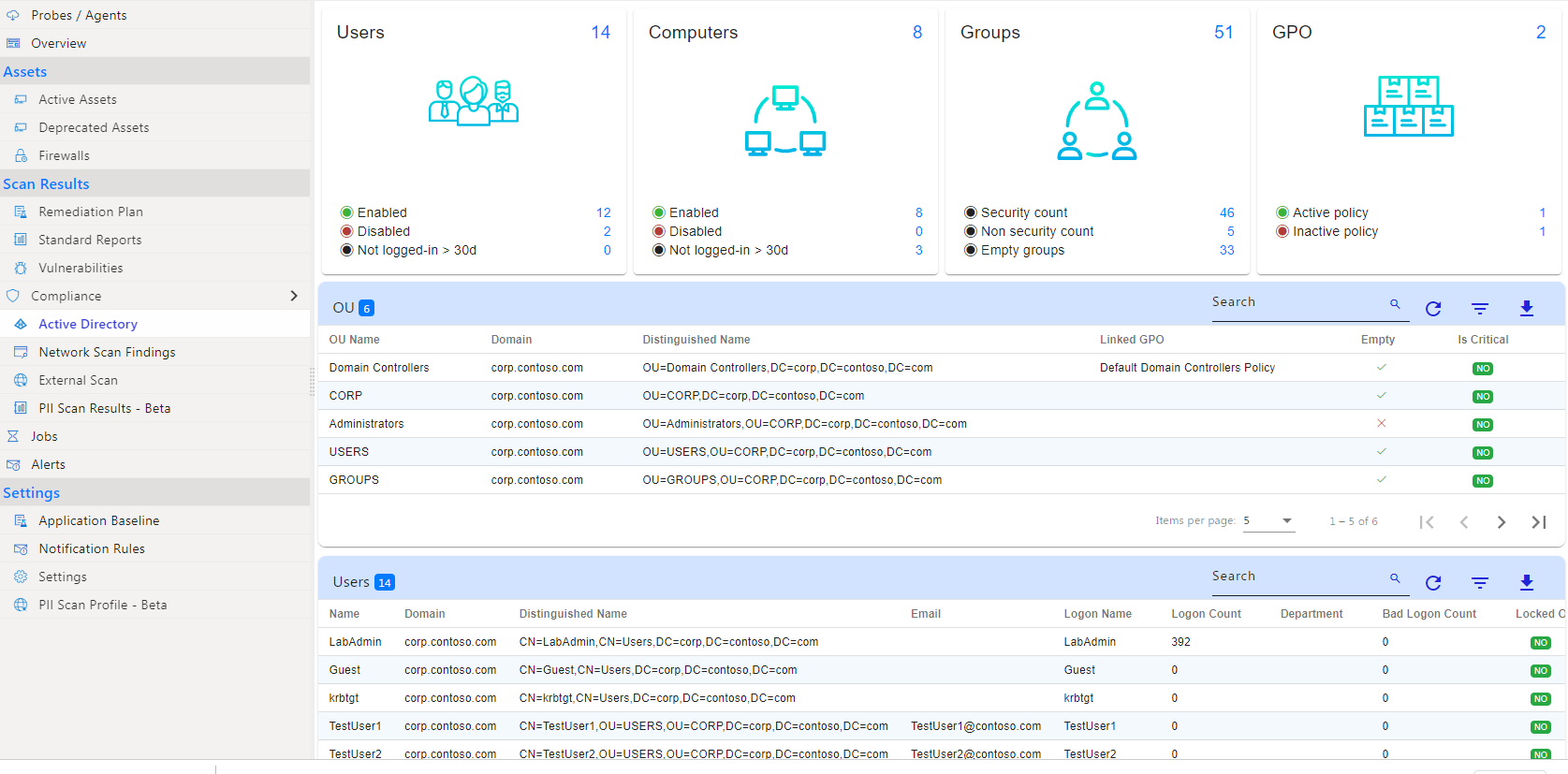
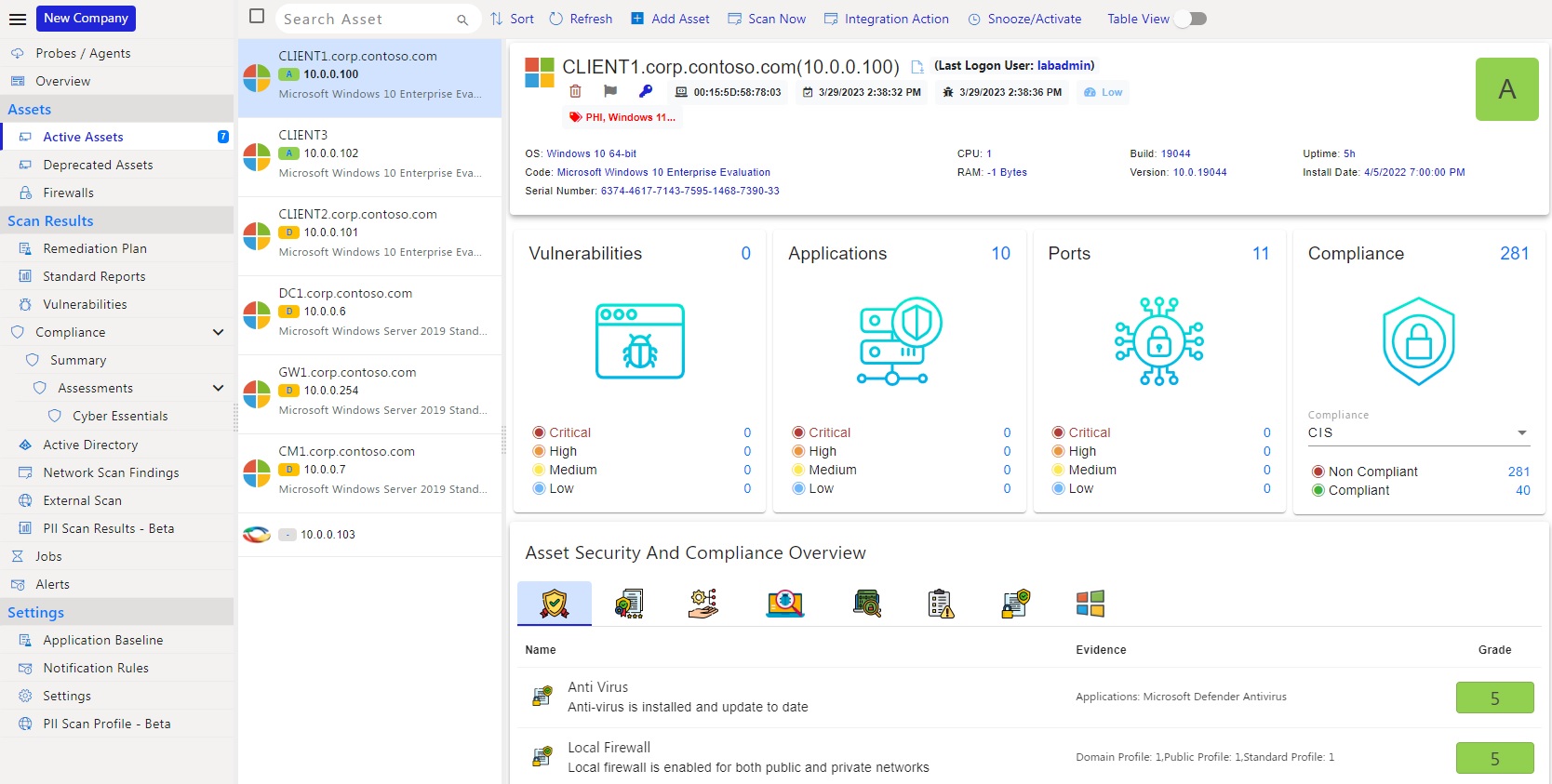
Technical Compliance Assessments
PCI-DSS Host-Based Technical Compliance Assessment
Background
PCI-DSS (Payment Card Industry Data Security Standard) compliance is essential for organizations that handle, process, or store cardholder data.
Goal: To protect cardholder data and reduce the risk of data breaches, fraud, and unauthorized access through a set of security requirements for clients that handle, process, or store payment card information.
Implement PCI-DSS standards to:
- To protect sensitive cardholder data.
- Reduce the risk of data breaches and unauthorized access.
- Demonstrate to your customers that you take their data security seriously.
- Comply with legal and regulatory compliance.
- Reduce financial and reputational risk.
Tool Summary
Road Map Technologies’ toolset is a cloud-native and multi-tenant vulnerability and compliance management platform that utilizes three different methods of deployment. Depending on the use case you can deploy it as a scanner, probe, or agent.
Deployment Methods:
- Scanner
- Allows for one-time scans of a network. These are primarily used for one-time assessments and can be ran from a single host on a network.
- Probe
- Allows for continuous assessments of a network and can be used for automatic scanning via scheduling. Only one probe per network is required. These also require credentials for a more effective scan.
- Agents
- Allows for continuous assessments of a network. Each endpoint is required to have an agent installed. It grants improved system visibility, reduces network load, and runs without passing credentials over the network.
Road Map recommends deploying one agent per endpoint and one probe per network for maximum efficiency, coverage, and discovery.
Assessment Summary
Road Map Technologies will assess a client’s compliance with PCI-DSS requirements and to ensure that appropriate security measures are in place to protect cardholder data.
Objectives
- Assess endpoint compliance.
- Identify security gaps and vulnerabilities.
- Assist in improving overall security posture.
- Offer guidance and recommendations.
One-time Assessments
- Verify cleanup of one-time scanner (One-time assessments only)
- Artifacts, VMs, or hardware
- Document findings in a report and have another analyst review and finalize it.
- Send the Finalized Report to client and schedule a call to discuss findings and remediations.
- Client closing call.
Ongoing Vulnerability Management Service (Probe or Agents)
- Finalize agent and probe installations.
- Complete the final policy tuning.
Ongoing Management
- Continuously monitor the performance of the agent and probe-based scanners.
- Regularly update the agent and probe scanners.
- Follow a vulnerability management routine and schedule that involves:
- Running periodic discovery scans (probes)
- Periodic compliance scans (agents and probes)
- Non-compliant Remediation
- Mitigation Verification
- Reporting
Metrics Measured
- Compliance Status
- Track overall PCI-DSS compliance, non-compliance, or partial compliance.
HIPAA Host-Based Technical Compliance Assessment
Background
HIPAA (Health Insurance Portability and Accountability Act) compliance is crucial for organizations that handle protected health information (PHI).
Goal: To protect the privacy and security of individual’s protected health information (PHI) by establishing a set of standards for organizations that handle, process, or store PHI data.
Implement HIPAA standards to:
- To safeguard protected health information (PHI).
- Reduce the risk of data breaches and unauthorized access.
- Demonstrate to your patients and partners that you prioritize the privacy and security of their health data.
- Comply with legal and regulatory compliance.
- Reduce financial and reputational risk.
Assessment Summary
Road Map Technologies will assess a client’s compliance with HIPAA regulations and to ensure that the required privacy and security measures are in place to protect individuals’ protected health information (PHI).
Objectives
- Assess endpoint compliance.
- Identify security gaps and vulnerabilities.
- Assist in improving overall security posture.
- Offer guidance and recommendations.
One-time Assessments
- Verify cleanup of one-time scanner (One-time assessments only)
- Artifacts, VMs, or hardware
- Document findings in a report and have another analyst review and finalize it.
- Send the Finalized Report to client and schedule a call to discuss findings and remediations.
- Client closing call.
Ongoing Vulnerability Management Service (Probe or Agents)
- Finalize agent and probe installations.
- Complete the final policy tuning.
Ongoing Management
- Continuously monitor the performance of the agent and probe-based scanners.
- Regularly update the agent and probe scanners.
- Follow a vulnerability management routine and schedule that involves:
- Running periodic discovery scans (probes)
- Periodic compliance scans (agents and probes)
- Non-compliant Remediation
- Mitigation Verification
- Reporting
Metrics Measured
- Compliance Status
- Track overall HIPAA compliance, non-compliance, or partial compliance.