Mergers, Acquisitions and Divestitures (MAD): Know Before You Grow
The MAD Journey
This journey is your road map to success when corporate decisions are made to merge, acquire or divestiture companies. Have you considered the total IT costs involved with your journey? We at Road Map Technologies can provide you with the necessary tools to make sure you are headed in the right direction.
We employ certified software asset managers and are proud to be an approved provider of the IAITAM – International Association of Information Technology Asset Managers and have staff with MAD experience.
The planning phase is important to ensure you have everything you need to begin your journey, so here are a few key questions to reflect upon.
Key Questions:
-
Is your transition plan efficient (time, cost and quality)?
- Is it a manual task of the IT department, or a data collection of information from SCCM and Active directory?
- How accurately and thoroughly has the IT team been mapping the data needed to either connect or disconnect the company in or out of the existing infrastructure?
-
Do you have hidden costs and obstacles such as:
- Do you have conflicts resulting from outdated hardware that may not operate properly with software applications?
- Unsupported software?
- Are you concerned with software license compliance issues that could result in fines with the vendor?
-
Do you have financing opportunities?
Can you leverage the cost of upgrades and licensing of the inventory against the purchase cost? Merger, acquisition, and divestitures processes are very complex to say the least. When the initial legal paperwork has been signed, everything must move swiftly and efficiently to include inventory and migration of the IT infrastructure. This usually must be done in less than 15 days with little to no interruption of daily processes.
How can you simplify the process and mitigate the risk?
Know Before You Grow!
What do you have?
Our system creates a thorough and accurate inventory of Active Directory, computers, servers, databases (SQL and Oracle), printers, tablets, phones, VMware, and Open Stack.
How is it connected?
The automated solution uses the inventory information and rationalizes the inventory. Specifically, it maps Active Directory groups to users, devices and applications.
Do You Have Opportunity or Risk in Your Licenses?
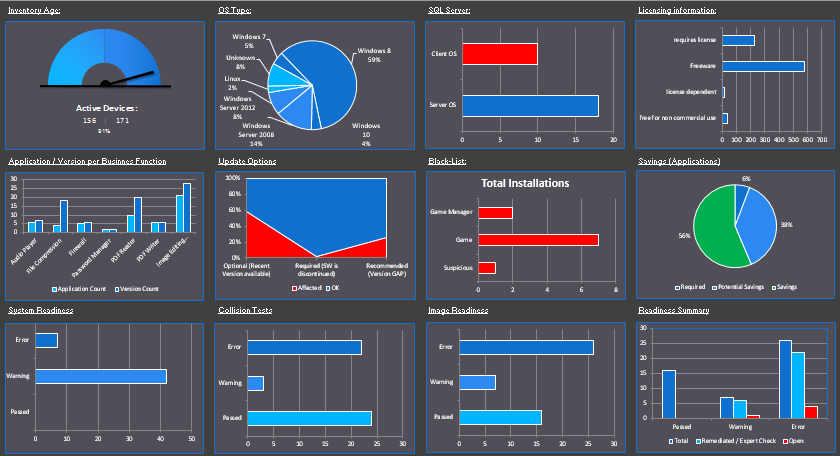
Next, the system maps user and application access to databases, mitigating the risk of downtime during migration. Visibility and Control: Being able to see a high level of overview and drilling down to specific users by user or device will provide the information needed to rationalize if the hardware and software is required after the migration. The process provides reports on how many devices each user uses in the environment, last logon for the devices, and all the applications across the devices to include the versions of the applications.
5-Step Rationalization Process
- Discovery
- Inventory
- Recognition and Summary
- Hardware and Software Rationalization
- Forecasting Costs of IT Ownership
Discovery
During discovery, the agentless client will discover devices by Active Directory, IP subnet or broadcast and report back. During the discovery phase, the agentless client can also inventory all Active Directory or selected parts of Active directory. The during this phase we will discover:
- Active Directory
- Users
- Devices
- Groups
- Computers
- Windows 95 – latest operating systems
- Linux
- IOS
- SQL Databases
- Oracle Database
- Hypervisors
- Network Printers
- Phones and tablets
Inventory
Upon completion of the discovery, we will inventory the devices, databases, hypervisors and applications. During the inventory phase, we harness the file server information to report on file shares and permissions. We provide reports for applications and devices, identifying platforms, OS, total number of application versions across the enterprise and install counts. The process will complete a full inventory on all Operating Systems (OSs) including all Windows, IOS, and Linux. Databases and permissions are inventoried during this phase as well. 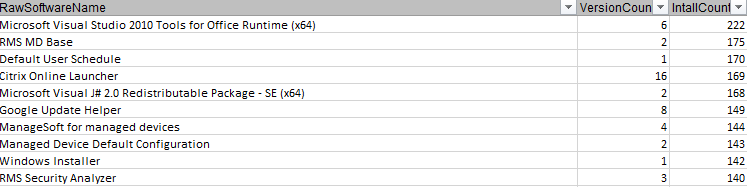
Recognition and Summary
During the Recognition and Summary step, Road Map Technologies links users, computers, Active Directory groups and applications. This step provides us with detailed reports that can be drilled down to the specific user, device, or application. Since we have the full and complete database inventory, we can map the security to the databases and file shares as well. 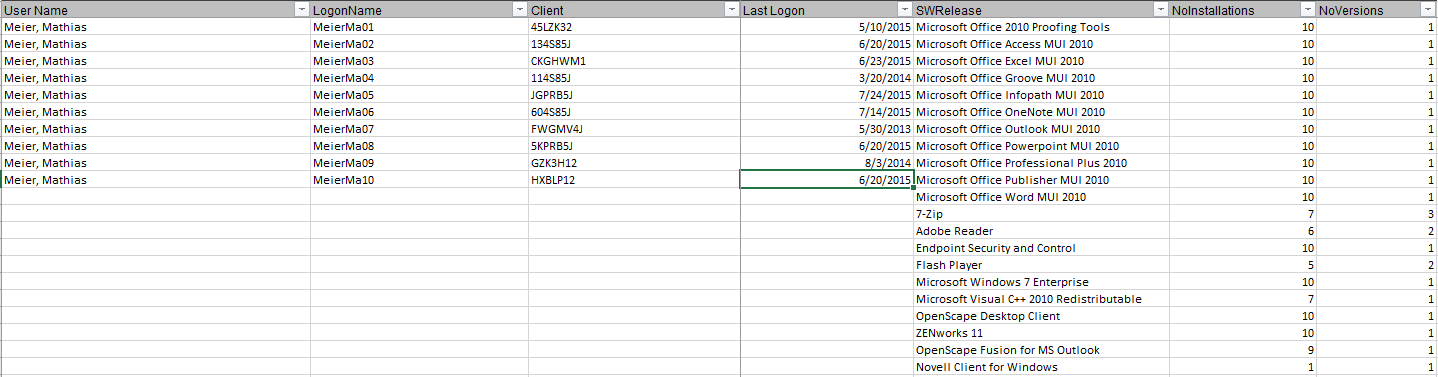
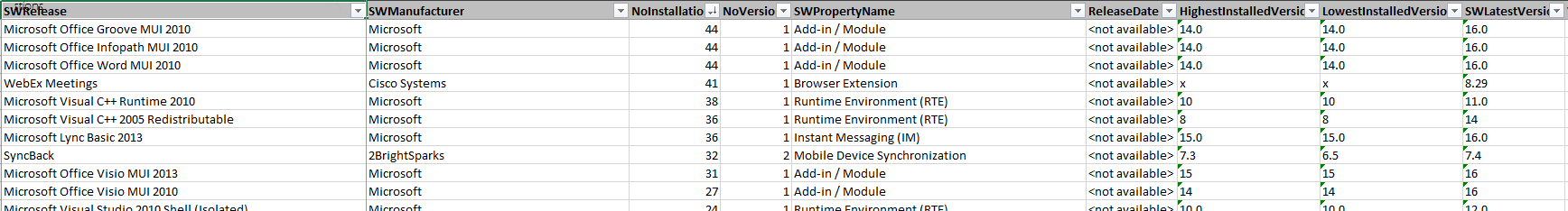
Rationalization
In the rationalization step, we work with the IT teams to optimize the systems and licenses, identifying what AD groups, hardware, and applications are required to keep. Application usage counts are provided to validate licensing compliance and identify what applications need to be moved over to the new infrastructure. During this rationalization step, we compare the inventory of the acquisition against the application inventory of the purchasing company to minimize the number of applications that need to be repackaged. We leverage API integrations for SNOW, SCCM, SmartTrack, Spider, Service Now, and others. During the rationalization, each device to be migrated is assessed for hardware requirements for the new OS platforms. Optional reports detail how many and which devices will not be supported on the preferred OS after the acquisition.
Forecasting IT Ownership and Costs
Visibility and Control: Based on the information collected and analyzed, we provide total pre and post-merger total cost of ownership of the IT infrastructure. It is information that may be able to be leveraged against the purchase. Specifically, if the IT inventory is quickly completed done once the intent to purchase is signed, why not leverage additional, previously unknown cost, against the purchase? Well, we’ll let the lawyers and banks figure that one out. Visibility gives managers more control! Upon completion of forecasting, you should have an accurate over view of:
- Cost of hardware replacement
- Application Licensing
- Audit concerns and potential loss will be identified
- Hardware and OS costs
- How many machines need to be replaced due to hardware requirements
- How many devices need to upgraded to latest OS
- Mapping reports available:
- Security groups to users
- Users to devices
- Users and devices to applications
- Users an devices to databases
- Other mappings as required
Conclusion
Mergers, acquisitions and divestures (MAD) inventory can be a complex and daunting task. When your staff does not have the correct tools, or experience, the IT portion of the MAD process can extend months longer than expected, costing valuable time, money or identifiable and mitigate-able risk. With an agentless solution, we provide visibility and control, identifying the IT inventory to help provide a decision on moving forward by rapidly mitigating unforeseen costs. Although we can retrieve a lot of inventory data with an agentless tool set, some things will still require an agent to retrieve user data. Such as:
- User mapped drives
- User defined printers
- User ODBC connections
- Per user installed applications
- Other user data not mentioned.
Whether you are using our tool or another inventory tool set such as SCCM or Snow, the same process applies to produce a complete view of the IT infrastructure, the foundation for a complete road map for the transition of IT. For best results, start “Discovery” as soon as possible during the MAD journey.
Are you ready for a reliable IT partner who will join you in the trenches and get it done right?