PriviCore

Most valuable asset is your sensitive information
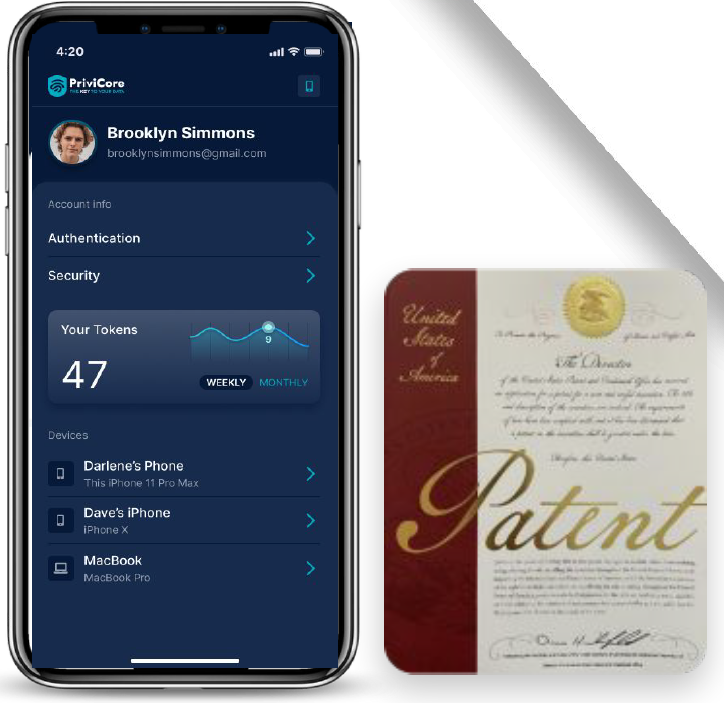
Privicore – Safeguarding your data to the max
One software engine, Four technologies
These technologies combined provides an unprecedented level of Data Security
Key benefits
Top-tier Industry Data Security
Unmatched protection against both external and insider threats, securing operational and backup data alike
Regulatory Compliance
Instantly meet standards like HIPAA, GDPR,NIS2, DORA with IT cost savings from reduced network segmentation needs and reduced cyber insurance premiums
Seamless Integration
Using a layered voting mechanism for access control supporting technologies like biometrics, behavioral analytics, blockchain device authentication and integration with 3rd party vendors while maintaining a user friendly experience for the end users
Future-Proof
Designed to adapt to evolving security challenges and regulations
Are you ready for a reliable IT partner who will join you in the trenches and get it done right?