By Howard Magill, CEO at Road Map Technologies
As most know, the CVE-2021-36934 is regarding overly permissive Access Control Lists (ACLs) on multiple systems files. One of these files is the Security Accounts Manager (SAM) Database. Details on identifying the vulnerability as well as the fix can be found at https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-36934.
For the purpose of identifying this vulnerability, some have directed me to https://github.com/JoranSlingerland/CVE-2021-36934/commit/e976fb1be2734c318c2deaaec4f01d83b9cb497f. I found this script not to find or return the correct information after some testing. Also, this script only works if ran directly on the devices.
Issue:
The purpose of the github script is supposed to identify any or all permissions not inherited. However, it is looking for specific accounts they may not exist or be affiliated with inherited permissions. Also, as previously stated, the script has to be ran on the local device.
Proposed Solution:
Create a PowerShell script that can be ran via SCCM leveraging PSADTK. Create an event log that can be picked up by Splunk and report in both SCCM and from Splunk.
Solution
Below is the PS script I put together. We leveraged PSADTK for ease of returning failure codes to SCCM. In this scenario, if the script fails due to client or other issues and does not run, it will not report in Splunk. We are writing keys to the registry for nonvulnerable and vulnerable. The SCCM detection method is set to be successful on nonvulnerable machines. This will allow us to report with SCCM. We are also writing to the System event log so Splunk will pick up vulnerable devices almost immediately. The script will also write the accounts that are not inherited to the log file. Keep in mind, if your SCCM client does not have access to read permissions on the file, it reports back as vulnerable.
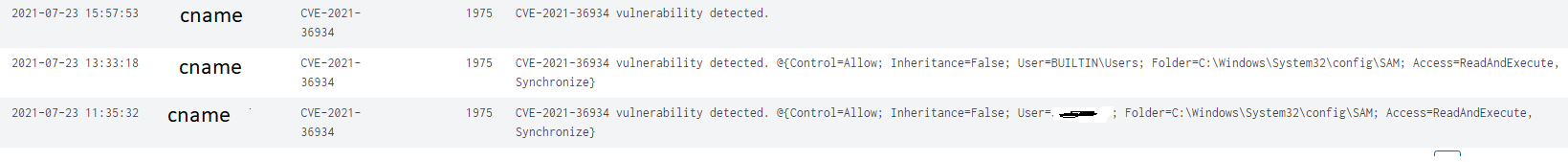
The below script will identify any account that is not inherited and write it to the event log and to the PSADTK log. Hope this helps someone. Feel free to ping us if you do not agree.
Step 1 Script
$getInheritances = Get-childitem C:\Windows\System32\config\SAM -recurse |
Get-Acl | % {
$path = $_.Path
$_.Access | where { $_.IsInherited -eq $false } | % {
New-Object PSObject -Property @{
Folder = $path.Replace(“Microsoft.PowerShell.Core\FileSystem::”, “”)
Access = $_.FileSystemRights
Control = $_.AccessControlType
User = $_.IdentityReference
Inheritance = $_.IsInherited
}
}
}
if (![string]::IsNullOrEmpty($getInheritances))
{
$checkvulnerability = Get-ItemProperty -Path HKLM:\SOFTWARE\[NAME] -Name “CVE202136934Check”
If (($checkvulnerability.CVE202136934Check -ne “Vulnerable”) -or ($checkvulnerability.CVE202136934Check -ne “”))
{
if ([System.Diagnostics.EventLog]::SourceExists(“CVE-2021-36934”) -eq $False)
{
New-EventLog -LogName “System” -Source “CVE-2021-36934”
}
Write-EventLog -LogName “System” -Source “CVE-2021-36934” -EventID ‘1975’ -EntryType “Info” -Message “CVE-2021-36934 vulnerability Remediated” -Category 1 -RawData 10, 20
Write-Log -Message “CVE-2021-36934 vulnerability found: $getInheritances” -Source ‘CVE-2021-36934’ -LogType ‘Legacy’
Set-RegistryKey -Key ‘HKEY_LOCAL_MACHINE\SOFTWARE\[NAME]’ -Name ‘CVE202136934Check’ -Value “NotVulnerable” -Type String
}
}
Else
{
Write-Log -Message “CVE-2021-36934 vulnerability not found” -Source ‘CVE-2021-36934’ -LogType ‘Legacy’
Set-RegistryKey -Key ‘HKEY_LOCAL_MACHINE\SOFTWARE\[NAME]’ -Name ‘CVE202136934Check’ -Value “NotVulnerable” -Type String
}
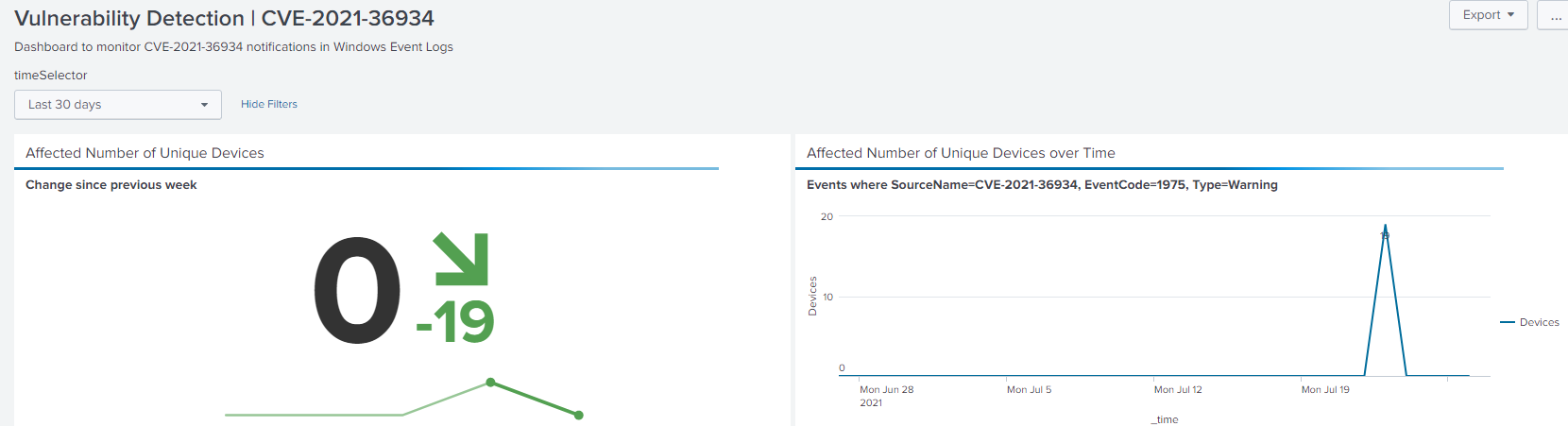
Step 2 Create Dashboard in Splunk
Hope this helps.
Feel free to contact us here.